Briefly Describe the Best Practice Rules for Firewall Use
For example a smart thermostats API may present a mode as a read-only property. Cyber Park is Now Open.

Azure Security Best Practices You Need To Know Cloud Academy
Mode commonly refers to what the thermostat.
. Looking to expand your knowledge on a particular subject matter. This means they are able to deliver high quality assignments. Please Use Our Service If Youre.
Use the dropdown box to either Accept or Mitigate the risk posed by not implementing the best practice. Looking to expand your knowledge on a particular subject matter. Wishing for a unique insight into a subject matter for your subsequent individual research.
Join our new Webinar Series April 21 2022 900am PDT 1200pm EDT. The description appears in the DESCRIPTION field of all Help views. Thank you for the assistance.
Briefly describe the activities of the assessment. A one stop shop for your gamified cyber security needs. Two or three full sentences that briefly list everything that the function can do.
Talk about the importance of information security at the client organization. The key is determining how you will approach the exam and then actively reading the questions. As YOU DESERVE THE BEST SECURITY Upgrade to our latest GA Jumbo.
Best available This refers to a group of writers who are good at academic writing have great writing skills but are new in our team of writers. The following terms were established when. Since we are not covering all of the beginner-level topics the purpose of this high-level review is to help you be mindful of the terminology and remind you how these components work together.
Interested in having your paper proofread. Designed for Linux and Windows email system administrators Scrollout F1 is an easy to use already adjusted email firewall gateway offering free anti-spam and anti-virus protection aiming to secure existing email servers old or new such as Microsoft Exchange Lotus Domino Postfix Exim Sendmail Qmail and others. Awesome job by the writer.
All Videos In One Space. Wishing for a unique insight into a subject matter for your subsequent individual research. This section will briefly review the essential building blocks of paginated report design that you will use as you apply different report recipes.
A top-ten list is used to highlight the ten most urgent issues. Read about the latest tech news and developments from our team of experts who provide updates on the new gadgets tech products services on the horizon. Objects provide an interface to other code that wants to use them but maintain their own internal state.
The skill is how you handle this information to make the best use of your time. Complete Book Of Discrete Mathematics and its application 7th Edition. The objects internal state is kept private meaning that it can only be accessed by the objects own methods not from other objectsKeeping an objects internal state private and in general making a clear division between its public interface and its private internal state is.
This writers are also assigned a. To support this use case WoT descriptions should describe the networked devices present in building subsystems and their data capabilities. However one approach that can work well is to start the.
Discuss security efforts that the organization has under taken. This means they recently joined the team. Needing assistance with how to format citations in a.
Advice on developing Managing information Approach The exam is 3 hours long. Needing assistance with how to format citations in a paper. This group of writers have passed strict English tests plus tests from their fields of specialization.
Assign a person or group responsible for mitigating or accepting the risk. Ive used this service 3 times and this was by far the best paper Ive received. The description begins with The function If the function can get multiple objects or take multiple inputs use plural nouns in the description.
Please Use Our Service If Youre. Highlight three major security issues discovered that could significantly impact the operations of the organization. For each identified activity or control describe the way in which the cooperative does not meet the best practice as captured in the Guide to Developing a Cyber Security and Risk Mitigation Plan.
These capabilities should be related to properties of the substances or media that a device is operating on. Built-in multilayer security levels make. No gossip no negative news no paparazzi photos.
The Internet or internet is the global system of interconnected computer networks that uses the Internet protocol suite TCPIP to communicate between networks and devices. Requiring help with paraphrasing your scholarly articles and managing plagiarism. There is no designated reading time at the start of the exam.
It is a network of networks that consists of private public academic business and government networks of local to global scope linked by a broad array of electronic wireless and optical networking.
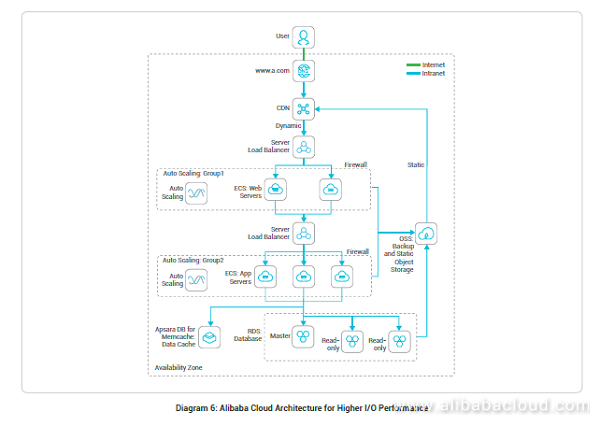
5 Best Practices For Different Web Application Hosting Scenarios Alibaba Cloud Community
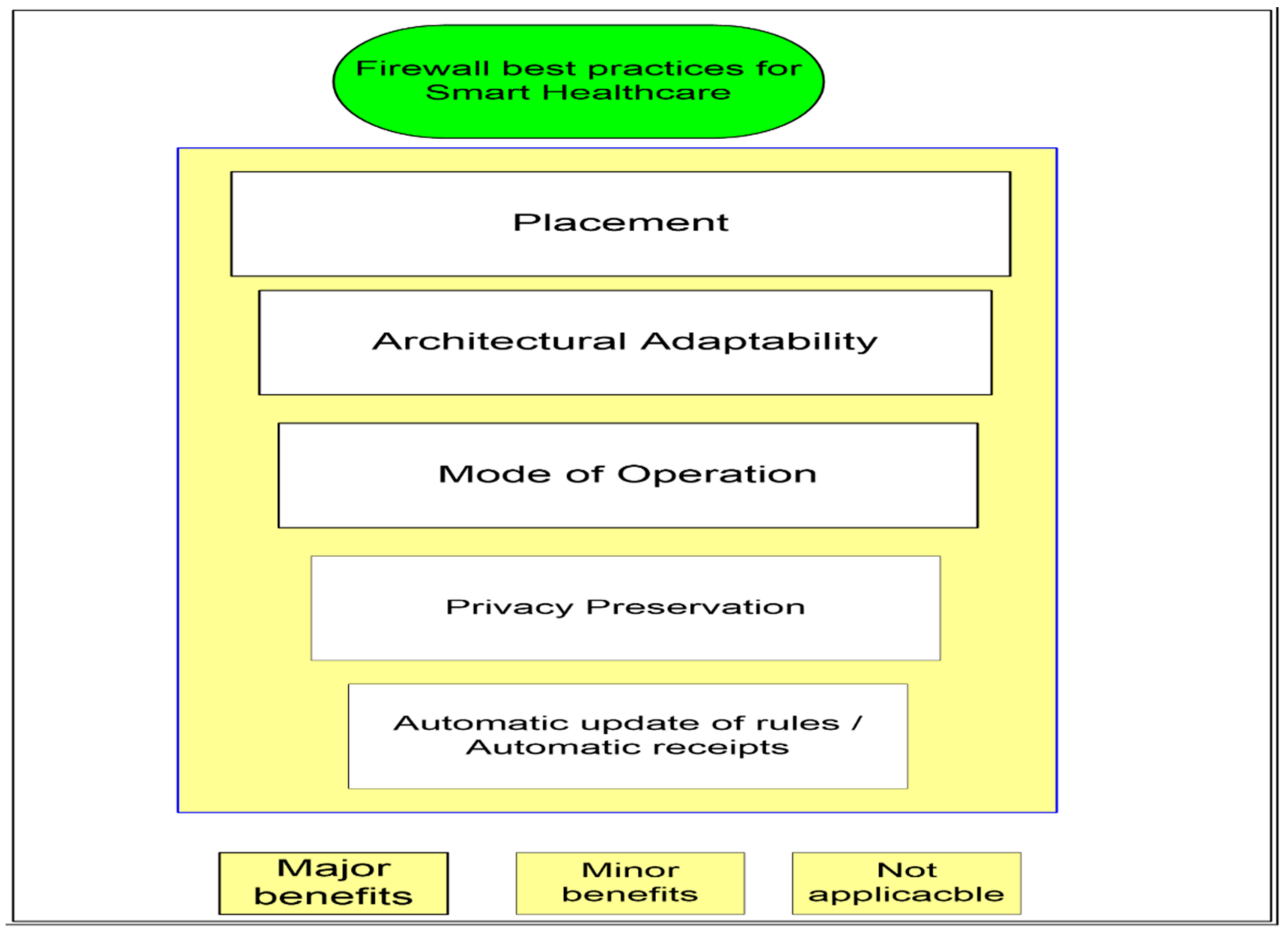
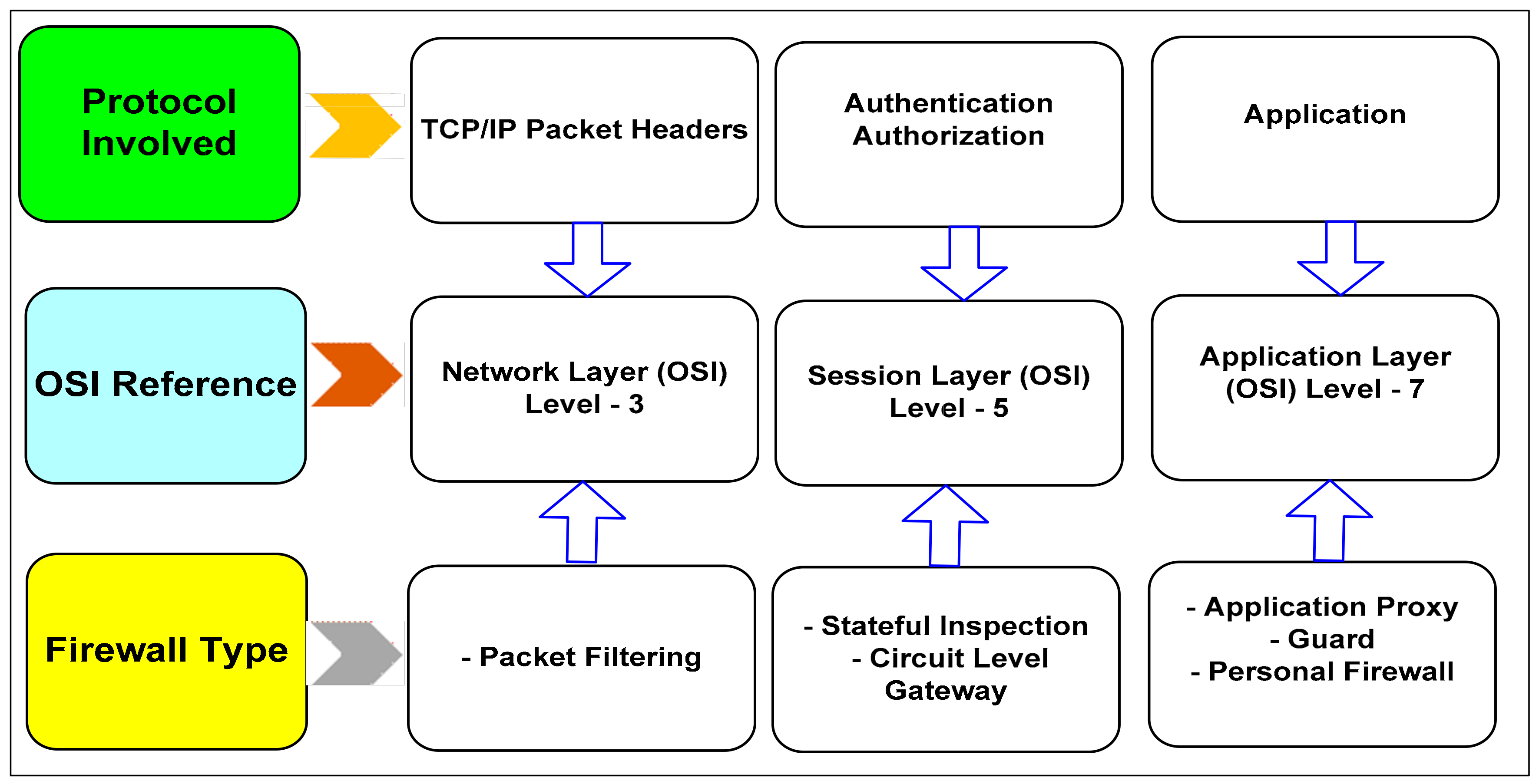
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
Hybrid Deployment Best Practices Microsoft Tech Community
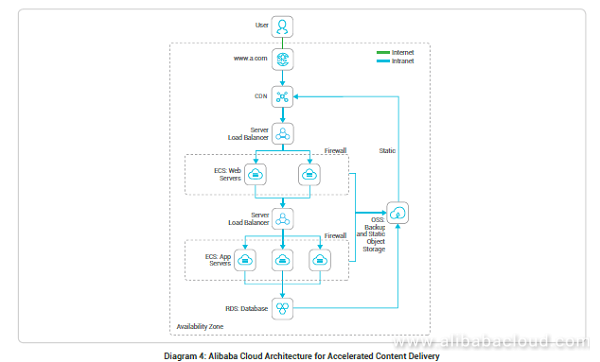
5 Best Practices For Different Web Application Hosting Scenarios Alibaba Cloud Community

Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html

Iso 27002 Best Practices For Information Security Management

Ibm Tivoli Network Manager Ip Edition Best Practices Guide 1 0 Manualzz
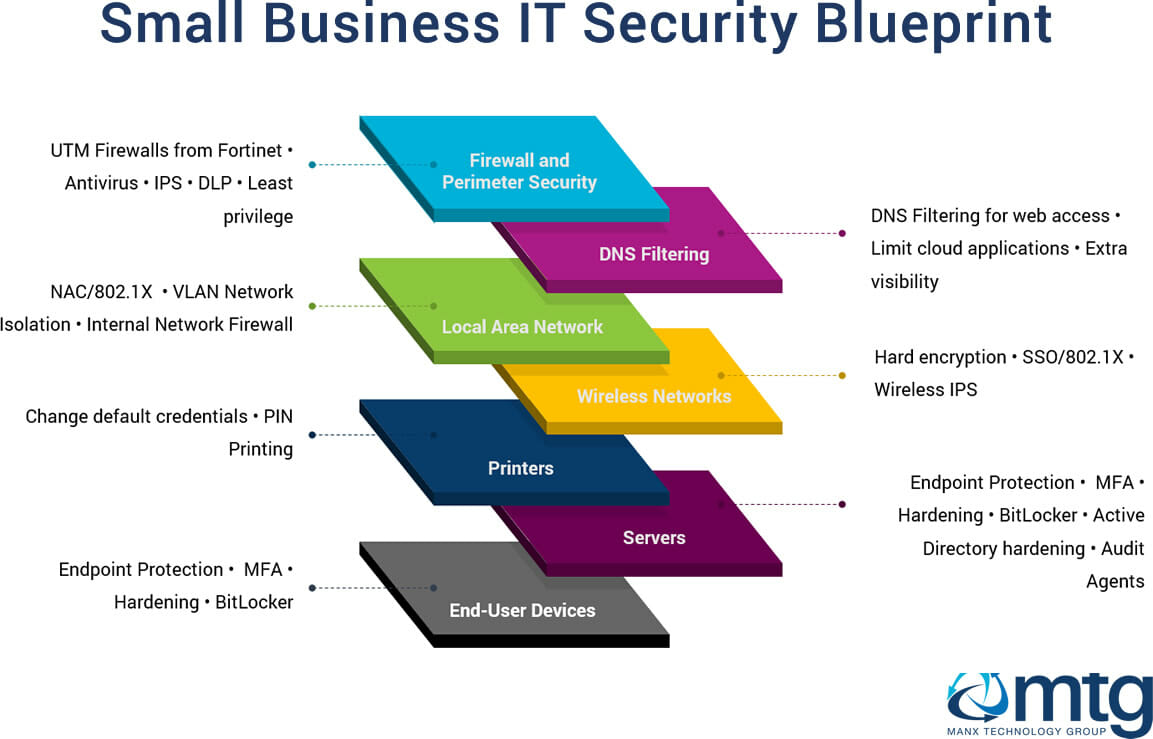
Small Business It Security Guide Manx Technology Group
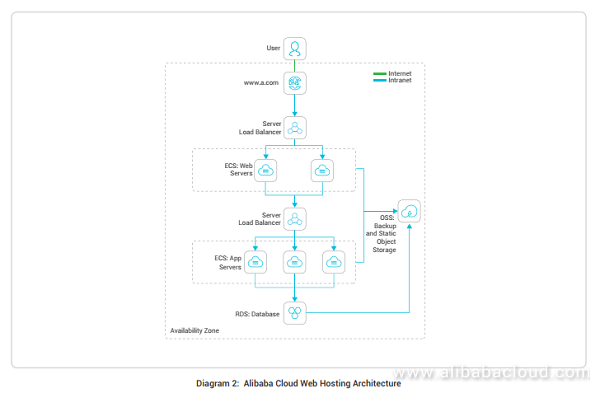
5 Best Practices For Different Web Application Hosting Scenarios Alibaba Cloud Community
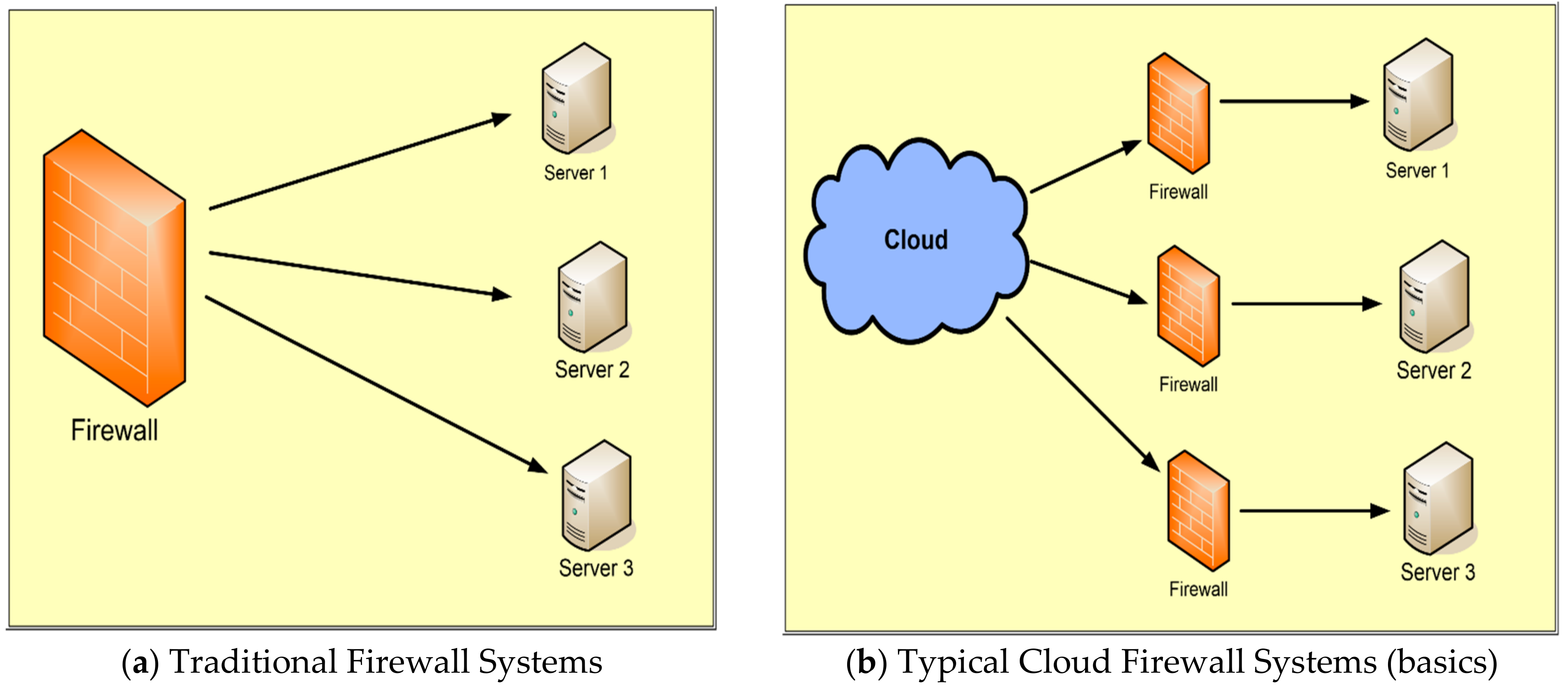
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
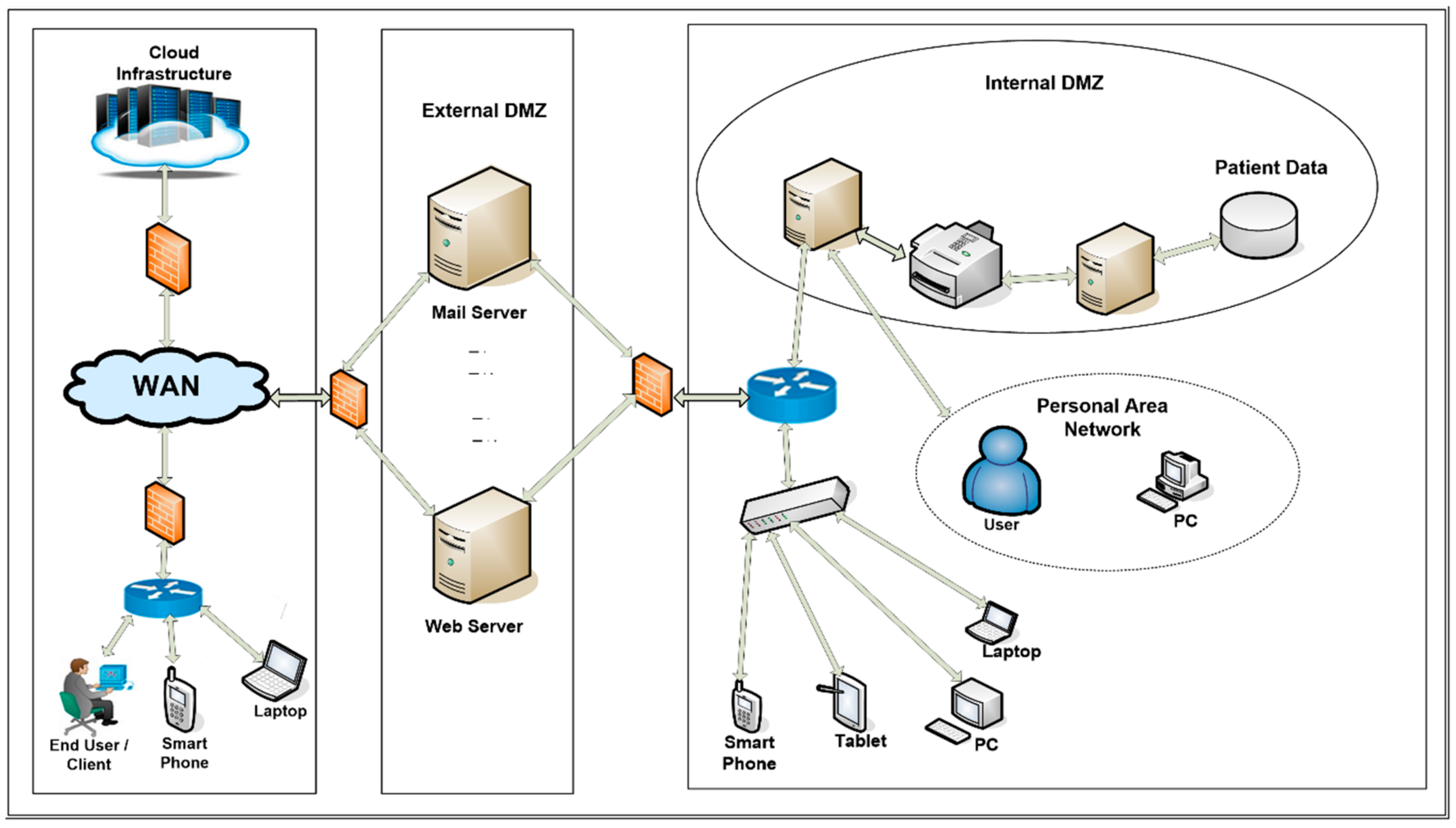
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
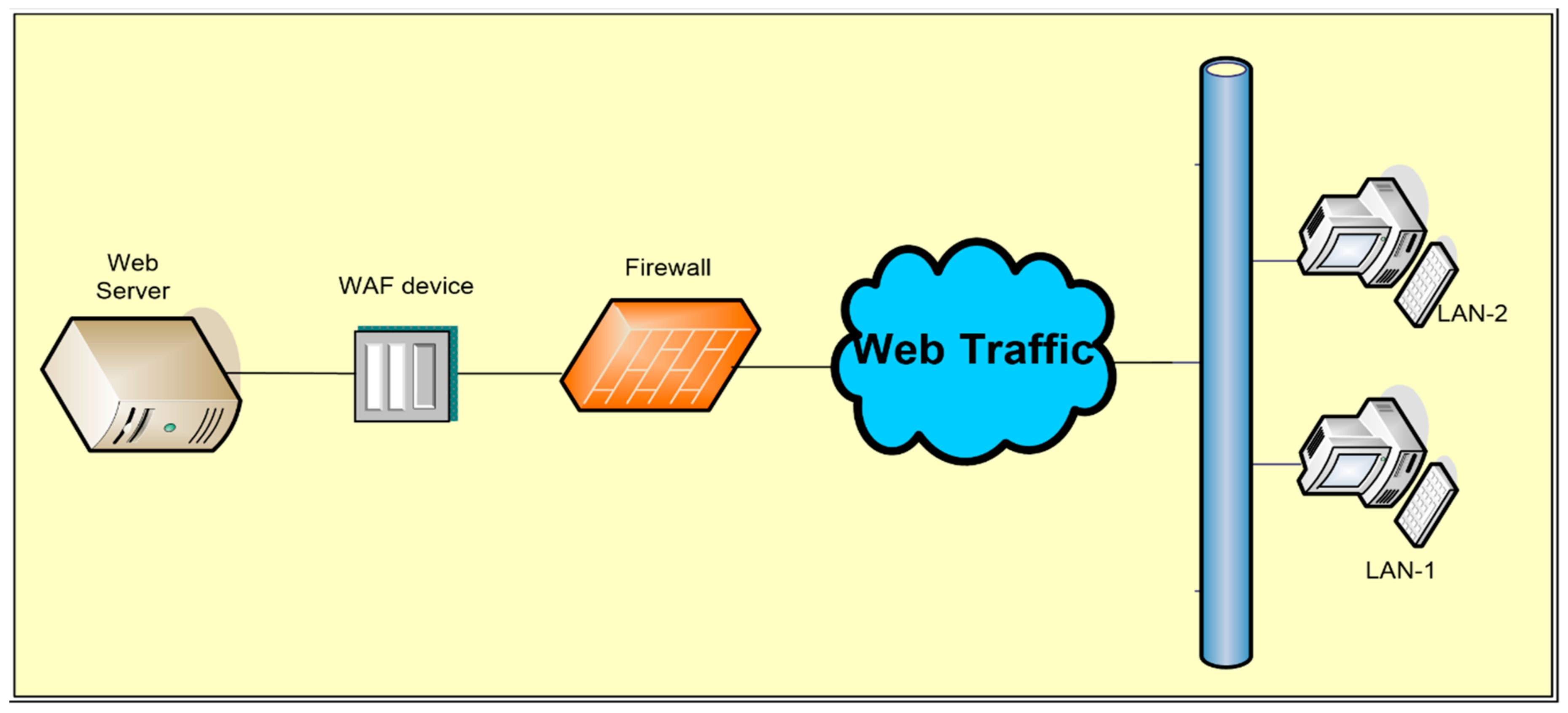
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
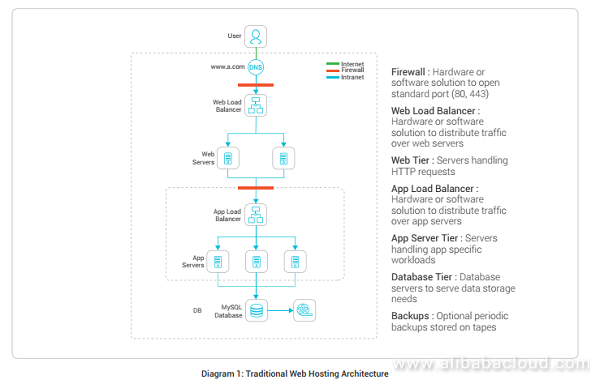
5 Best Practices For Different Web Application Hosting Scenarios Alibaba Cloud Community

What Is A Firewall Definition Key Components And Best Practices Toolbox It Security

Ccna 3 V7 Modules 3 5 Network Security Exam Answers

Best Practice Of Spring Cloud Application On Kubernetes High Availability Develop Paper

Network Rightsizing Best Practices Guide
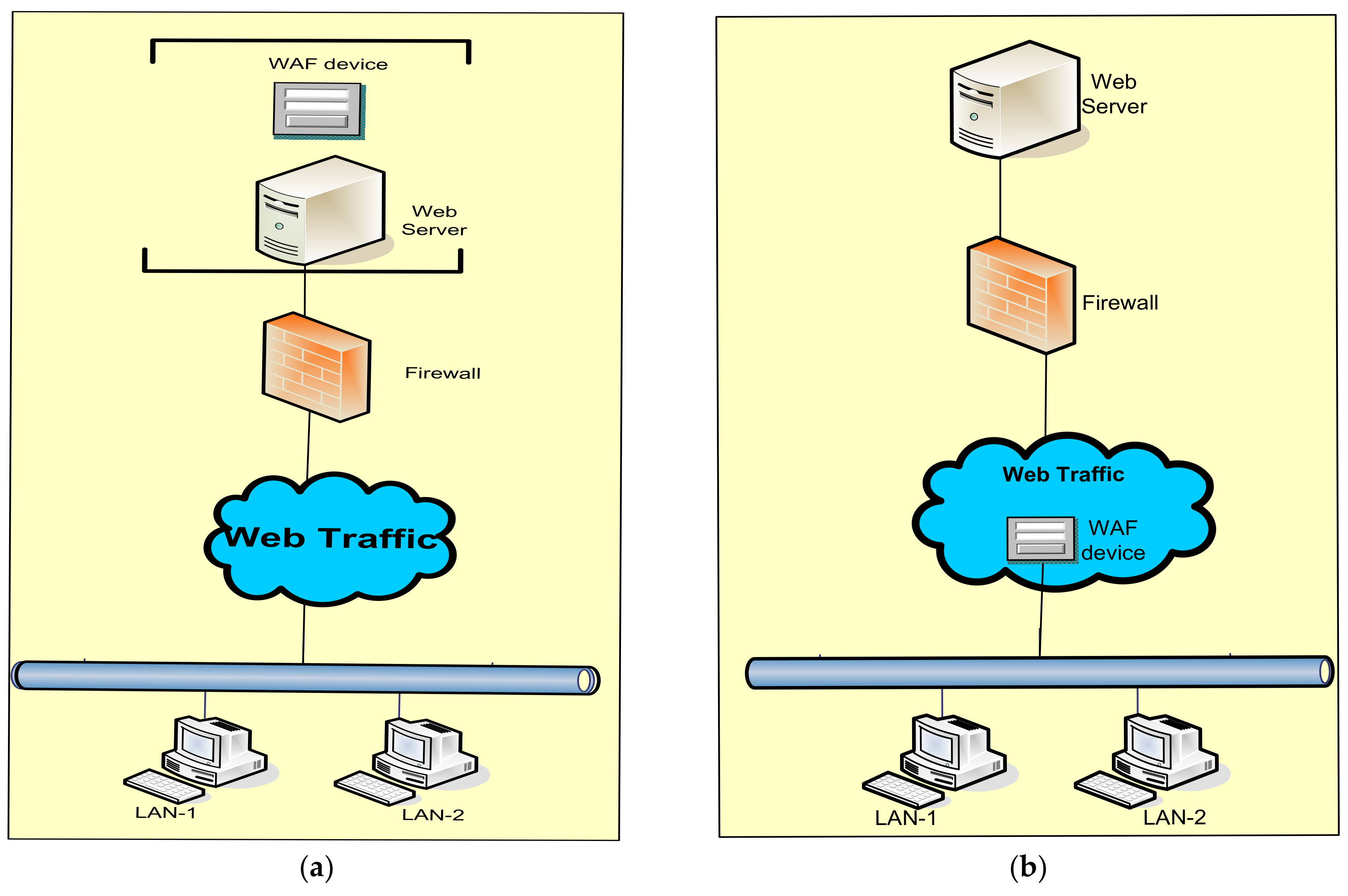
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
